;添加AddNative Hook的过程
AddNativeHooks proc
push_offset_RLC T("(Hunit;R)V")
lea edx, RLC(T("SetUnitX"))
lea ecx, RLC(JNSetUnitXHook)
GameCall PAddNative
push_offset_RLC T("(IRR)Hitem;")
lea edx, RLC(T("CreateItem"))
lea ecx, RLC(JNCreateItemHook)
GameCall PAddNative
ret
AddNativeHooks endp
;异常处理函数,处理DRx产生的异常
BreakpointHandler proc uses esi ebx pExceptionRecord:DWORD, pFrame:DWORD,
pContext:DWORD, pDispatcherContext:DWORD
GetBase
mov esi, pExceptionRecord
mov eax, (EXCEPTION_RECORD ptr [esi]).ExceptionCode
.if eax != EXCEPTION_SINGLE_STEP
mov eax, ExceptionContinueSearch
ret
.endif
mov eax, (EXCEPTION_RECORD ptr [esi]).ExceptionAddress
sub eax, RLC(hGameDll)
add eax, GameOriginalBase
mov edx, pContext
.if eax == PInitNatives
lea eax, RLC(PInitNativesHook)
mov (CONTEXT ptr [edx]).regEip, eax
.elseif eax == JNCreateUnit
lea eax, RLC(JNCreateUnitHook)
mov (CONTEXT ptr [edx]).regEip, eax
.endif
xor eax, eax
ret
BreakpointHandler endp
END START
6.Loader
;这个很简单了,就不做注释了
.386
.model flat, stdcall
option casemap :none
include windows.inc
include user32.inc
include kernel32.inc
include masm32.inc
includelib user32.lib
includelib kernel32.lib
includelib masm32.lib
include macro.asm
GetProcessIdByName proto :DWORD
.data
bCode db 0C00h dup(0) ;为上文的代码预留的空间,编译后通过别的程序写入
bCodeEnd dd 0
.data?
buffer db MAX_PATH dup(?)
hProc dd ?
dwPid dd ?
pMem dd ?
.CODE
START:
invoke GetModuleHandle, offset CTEXT("ntdll.dll")
invoke GetProcAddress, eax, offset CTEXT("RtlAdjustPrivilege")
push offset buffer ; old enable
push 0 ; current thread ?
push 1 ; enable ?
push 14h ; 14h = SE_DEBUG_PRIVILEGE
call eax
.while 1
invoke GetProcessIdByName, offset CTEXT("war3.exe")
.break .if eax
invoke Sleep, 500
.endw
mov esi, eax
invoke OpenProcess, PROCESS_CREATE_THREAD OR PROCESS_VM_OPERATION OR
PROCESS_VM_WRITE, NULL, esi
mov hProc, eax
invoke VirtualAllocEx, eax, NULL, 1000h, MEM_COMMIT,
PAGE_EXECUTE_READWRITE
mov pMem, eax
invoke WriteProcessMemory, hProc, pMem, offset bCode, offset bCodeEnd -
offset bCode, offset buffer
invoke GetModuleHandle, CTEXT("kernel32.dll")
invoke GetProcAddress, eax, CTEXT("GetProcAddress")
invoke CreateRemoteThread, hProc, NULL, NULL, pMem, eax, NULL, offset
buffer
invoke MessageBox, 0, offset CTEXT("Loaded!"), offset CTEXT("Proton's Dota
Cheater"), MB_ICONINFORMATION
invoke ExitProcess,0
GetProcessIdByName proc uses esi ebx lpProcessName:DWORD
LOCAL pe:PROCESSENTRY32
invoke CreateToolhelp32Snapshot, TH32CS_SNAPPROCESS, NULL
mov esi, eax
mov eax, sizeof PROCESSENTRY32
mov pe.dwSize, eax
lea ebx, pe
invoke Process32First, esi, ebx
assume ebx: ptr PROCESSENTRY32
.while TRUE
invoke Process32Next, esi, ebx
.break .if eax == 0
invoke CompareString, LOCALE_USER_DEFAULT, NORM_IGNORECASE,
lpProcessName,
-1, addr [ebx].szExeFile, -1
.if eax == 2
mov eax, [ebx].th32ProcessID
ret
.endif
.endw
xor eax, eax
ret
assume ebx: nothing
GetProcessIdByName endp
end START
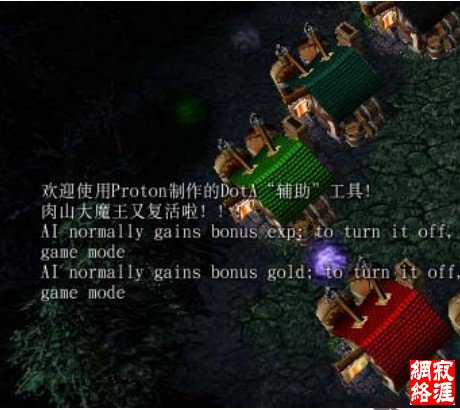
实际使用
在 Windows 7(6.1.7600)、魔兽争霸1.24e、浩方电竞平台5.6.0.311上测试成功,并
且在多次使用后账号积分没有变Lv-10。
弱点
尽管写的很隐蔽,但是弱点不是一点没有。首先就是DRx寄存器的使用,这东西是亮点也是
最大的硬伤——除了壳、调试器和一些邪恶的程序就没再有什么东西使用这个了。 |